Today’s drivers and passengers want a digital experience that mirrors their current digital experience — rich graphics, seamless connectivity, smart interfaces, app stores and more.
In response, global automakers and their Tier 1 suppliers are incorporating hundreds of millions of new lines of software to a growing number of automotive Electronic Control Units (ECUs) — new software from diverse suppliers with a wide range of requirements for system safety, security and robustness. Traditionally, this would require the addition of more ECUs, which would increase cost, cabling, complexity, weight and space. Instead, the emerging alternative approach to ECU duplicationi is ECU consolidation to combine multiple mixed functions and ECUs into fewer or single vehicle ECUs.
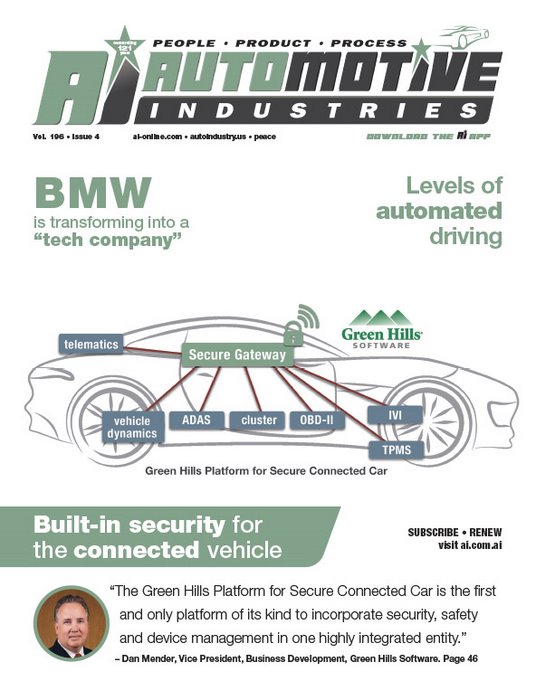
Green Hills Software, a global leader in high-assurance real-time operating systems (RTOS) and secure, embedded virtualization, deploys its safe and secure INTEGRITY RTOS as the foundation for its range of automotive platforms. The trusted 64-bit INTEGRITY run-time architecture is supported by Green Hills ASIL D qualified development tools, embedded FIPS 140-2 cryptographic tool kits and cloud-based secure credential management systems.
The combined scalable connected car platform enables global carmakers and their suppliers to bring new levels of safe and secure mixed criticality consolidation to the software-defined vehicle cockpit, combining safety-certified instrument clusters, multi-screen in vehicle entertainment and vehicle-critical control and information.
In June 2017 Green Hills Software and its subsidiary INTEGRITY Security Services (ISS) introduced its Platform for Secure Connected Car, featuring the industry’s most comprehensive solution for vehicle and smart city manufacturers building vehicle-to-anything (V2X) and European car-to-anything (C2X) On-Board Units (OBU) and intelligent transportation infrastructure.
Automotive Industries (AI) asked Dan Mender, Vice President, Business Development, Green Hills Software, what makes the connected car a game changer and why is security such an issue.
Mender: The connected car represents the next stage in the evolution of motor vehicle safety beyond what current vehicle-resident technologies like in-vehicle cameras and sensors can provide, by employing omnidirectional radio signals that deliver 360-degree coverage and the ability to “see” around corners and “see” through other vehicles. For the first time, unfamiliar vehicles and roadside units on untrusted public networks will be able to communicate with a vehicle’s On-Board Units (OBU) — with no human involvement — and influence life-critical vehicle actions and decisions.
Whereas functionality, performance and safety have been the traditional foundation for automotive software, the connected car demands authentication, identification and separation of critical software components running in a routinely insecure environment for the operational lifespan of the vehicle. The widespread adoption of Advanced Driver Assist Systems (ADAS) has the potential to dramatically improve vehicle safety by detecting dangerous situations and avoidance. However, these benefits will be rendered useless if it is possible for a malicious agent to hack the system and affect its performance.
AI: How serious are the risks of such cyber attacks?
Mender: Well, the way to judge this is to look at the motivation and opportunity of those who would initiate vehicle attacks. As cars incorporate more computing power and become more connected they start to resemble IT systems – only traveling at high speeds in the public domain. Hackers are increasingly targeting the IT systems of corporations and public bodies and causing disruption, largely for monetary gain. The 2017 WannaCry cyber attack held organisations, including medical and transport services, to ransom is a prime example of the potential risks. As vehicles become more connected, and ultimately autonomous, the attack surface will rise and so will the opportunities for hackers. And the terrible consequences of a fleet of autonomous trucks being remotely hijacked means that any hacker who achieves this would be in a strong position to extort a significant ransom.
AI: What are the security challenges associated with development of autonomous and highly automated cars?
Mender: The first point to make is that you cannot retrofit security. System architecture must be designed to be secure from the beginning, and without that your car cannot be safe. That said, there is a lot of pre-existing software and applications that automakers (and consumers) want to run in cars.
This includes embedded Linux, Android and other consumer operating systems whose use people want to extend into the automotive environment. It’s well known that the millions of lines of code in these high level OSes hold thousands of known security vulnerabilities, concealing many possible entry points for hackers. Add to this the fact that more applications and processes within the car are being integrated into the same subsystem on a single multicore processor, and it is clear that the opportunities for interference or security breaches to jump from sub-system to sub-system are substantial. Communication between cars and infrastructure coupled with the growth in ECU complexity multiplies the security challenge a hundredfold.
AI: How is your company meeting these challenges?
Mender: At Green Hills Software we start with a natural advantage because for decades we have been helping our customers develop software for high performance, life critical and mission critical systems, such as in the avionics sector, where there is zero tolerance for failures or system compromises. For these systems we based their designs on our INTEGRITY RTOS, which has been independently accessed to achieve the highest levels of reliability and security with unprecedented Common Criteria EAL 6+ credentials and ISO 26262 ASIL D safety certification.
Building on this, we added INTEGRITY Multivisor secure virtualization, which allows guest operating systems, such as Linux and Android, to be safely and securely virtualized alongside system-critical services and applications on a single multicore hardware platform. From this, we have developed a family of complementary applications and services and brought them together to form the unprecedented Green Hills Platform for Secure Connected Car.
AI: What makes your connected car platform different from others?
Mender: The Green Hills Platform for Secure Connected Car is the first and only platform of its kind to incorporate security, safety and device management in one highly integrated entity. It provides a clear path for OEMs and Tier 1s to immediately address the range of challenges to design, develop and deploy the most secure and safe V2V solution for the next generation of vehicle awareness as outlined in the US Department of Transportation (US DOT) New Proposed Rule Making (NPRM), Docket number NHTSA-2016-0126.









More Stories
Towing Services Explained: 6 Key Facts You Need to Know
Environmental Factors That Influence Ceramic Coating Choices
Professional vs. DIY Tinting: What You Should Know